Extreme Wireless
(→RADIUS Server) |
|||
| Line 10: | Line 10: | ||
* '''Firewall Friendly External Captive Portal (FF-ECP):''' describes a variation on the wireless controller’s External Captive Portal (ECP) support that addresses customers who use a public cloud-based ECP. Redirect the browser to the controller to approve the user. | * '''Firewall Friendly External Captive Portal (FF-ECP):''' describes a variation on the wireless controller’s External Captive Portal (ECP) support that addresses customers who use a public cloud-based ECP. Redirect the browser to the controller to approve the user. | ||
| − | + | CoffeeBean Wi-Fi Platform uses RADIUS servers to authenticate users and is a service in the cloud, so the more appropriate approach to integrate with the platform is the Firewall-Friendly External Captive Portal (FF-ECP). | |
This guide was created using the following components: | This guide was created using the following components: | ||
| Line 147: | Line 147: | ||
* DHCP Server (0.0.0.0/0:67, UDP) | * DHCP Server (0.0.0.0/0:67, UDP) | ||
| − | You’ll need to add policy rules to the services used by the | + | You’ll need to add policy rules to the services used by the CoffeeBean Captive Portal. See the list of [[Walled_Garden_for_the_Social_Login|hostnames]] in Walled garden and add the ones you use as matching patterns in the group Web Applications. |
Revision as of 14:24, 14 May 2019
Contents |
Introduction
This guide describes the configuration steps to enable an external captive portal in the cloud-based network controller ExtremeWireless.
ExtremeWireless provides multiple approaches to configure External Captive Portals (ECP):
External Captive Portal:
- External Authorization (ECPEA): is a variant of ECP where the web server is responsible for contacting any back-end authentication server in order to verify a user’s credentials and to determine the access control role to assign to a station. It’s required to call an API to approve the user and handle the response.
- External Captive Portal: Internal Authorization (ECPIA): is a variant of captive portal where the captive portal web server is hosted on the controller and relies on the controller to handle authenticating and authorizing the station. The controller uses one or more external RADIUS servers to perform authentication and authorization of credentials. It’s required to call an API to approve the user and handle the response.
- Firewall Friendly External Captive Portal (FF-ECP): describes a variation on the wireless controller’s External Captive Portal (ECP) support that addresses customers who use a public cloud-based ECP. Redirect the browser to the controller to approve the user.
CoffeeBean Wi-Fi Platform uses RADIUS servers to authenticate users and is a service in the cloud, so the more appropriate approach to integrate with the platform is the Firewall-Friendly External Captive Portal (FF-ECP).
This guide was created using the following components:
Controller: ExtremeWireless Version: 10.01.02
VNS Wizard
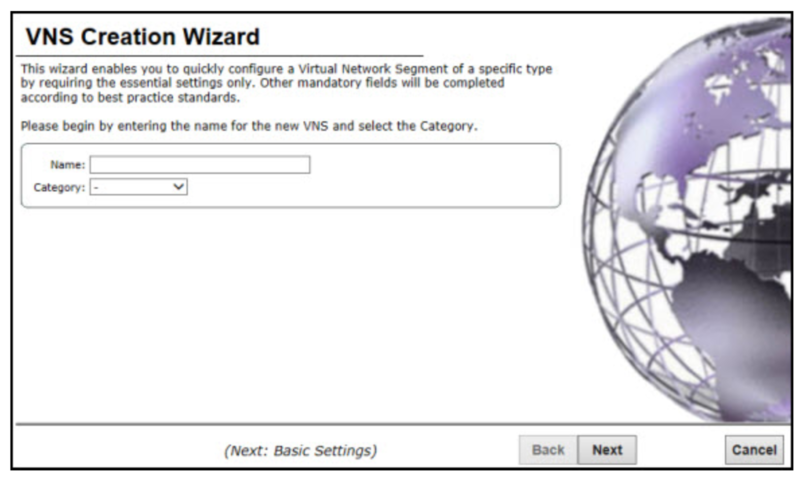
To configure a Firewall Friendly External Captive Portal VNS using the VNS wizard:
- From the top menu, click VNS. The Virtual Network Configuration screen displays.
- In the left pane, click New, then click START VNS WIZARD. The VNS Creation Wizard screen displays.
Configure the following options:
- Name: type a name for the Firewall Friendly Captive Portal VNS
- Category: select “Captive Portal”
Click next continue to configure.
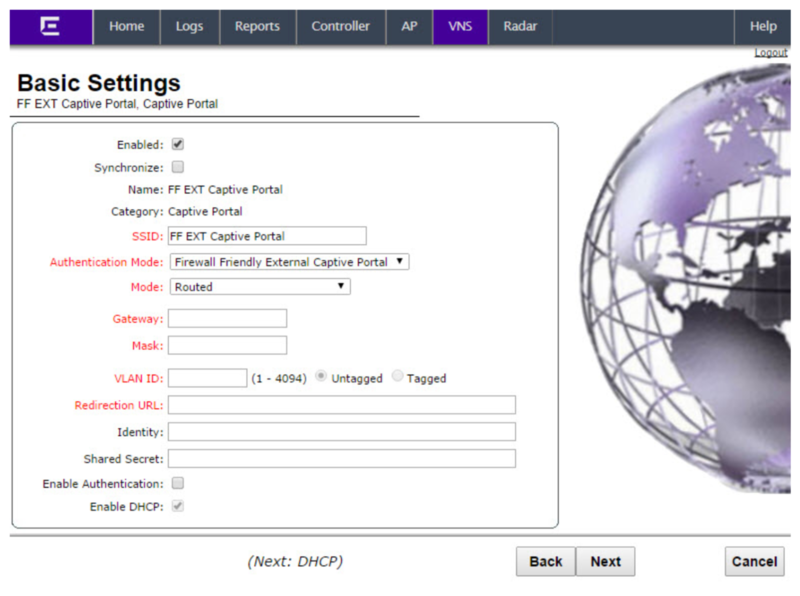
Basic Settings
The Basic Settings screen displays:
Configure the following options:
- Enabled: checked
- SSID: type a name for the SSID
- Authentication Mode: select “Firewall Friendly External Captive Portal”
- Mode: select “Routed”
- Gateway: 192.168.101.1 (or whatever you like)
- Mask: 255.255.255.0 (or whatever you like)
- VLAN ID: 50 and ensure “Untagged” is selected.
- Redirection URL: the provided captive portal login URL
- Identity: must be left empty
- Shared Secret: must be left empty
- Enable Authentication: checked
- Enable DHCP: checked
Click next to continue to configure.
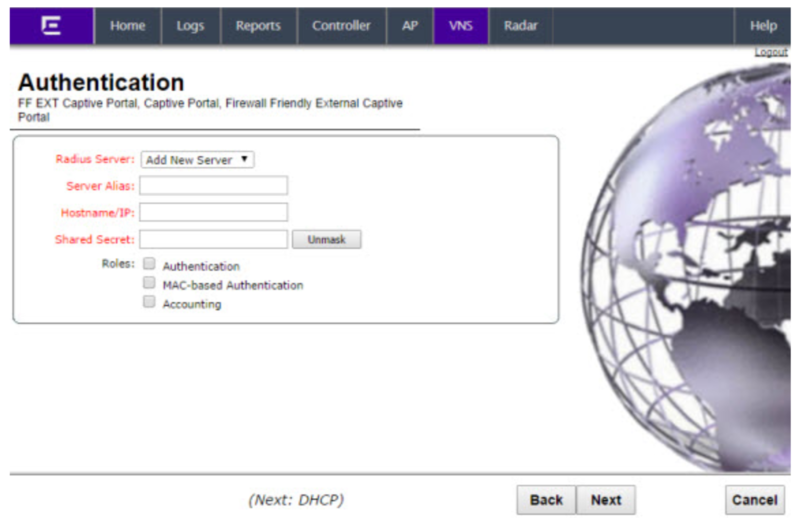
Authentication
Configure the following options:
- Radius Server: click “Add New Server”.
- Server Alias: Type a name you want to assign to the new RADIUS server.
- Hostname/IP: the RADIUS server hostname according to your environment/region.
- Shared Secret: the provided RADIUS client secret.
- Roles: check “Authentication” and “Accounting”.
Click next. The DHCP screen displays.
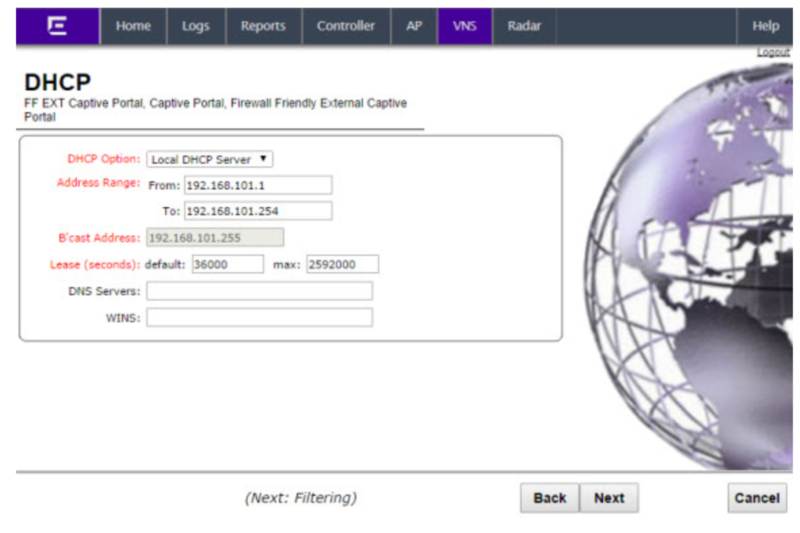
DHCP
The DHCP screen displays:
Configure the following options:
- DHCP Option: click “Local DHCP Server”
- Address Range: from 192.168.101.1 to 192.168.101.254 (or whatever you like)
- Lease: keep default values
- DNS Servers: 8.8.8.8 (or whatever you like)
Click next. The Filtering screen displays.
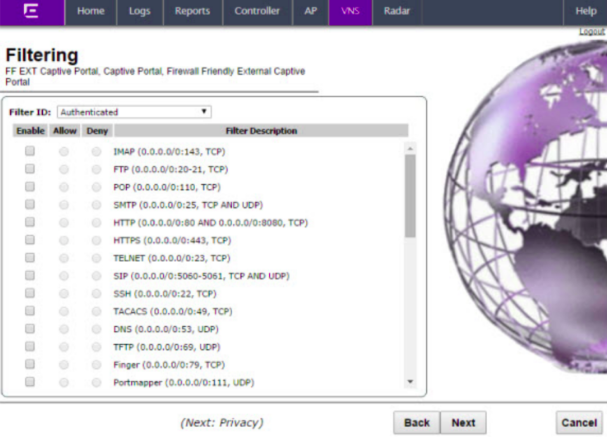
Filtering
The Filtering screen displays:
Select Non-Authenticated in Filter ID.
Enable and allow the following filters:
- DNS (0.0.0.0/0:53, UDP)
- DHCP Server (0.0.0.0/0:67, UDP)
Enable and deny the following filters:
- (0.0.0.0/0)
Click next. The Privacy screen displays.
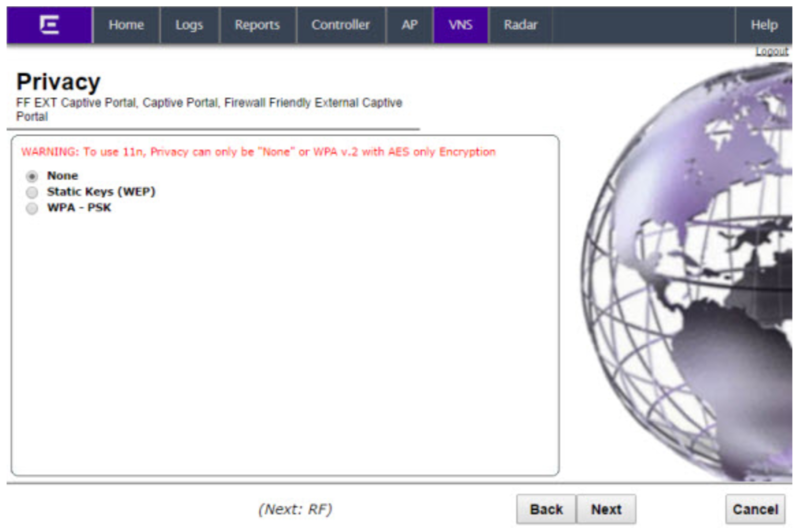
Privacy
The Privacy screen displays:
Select None and click next. The Radio Assignment screen displays.
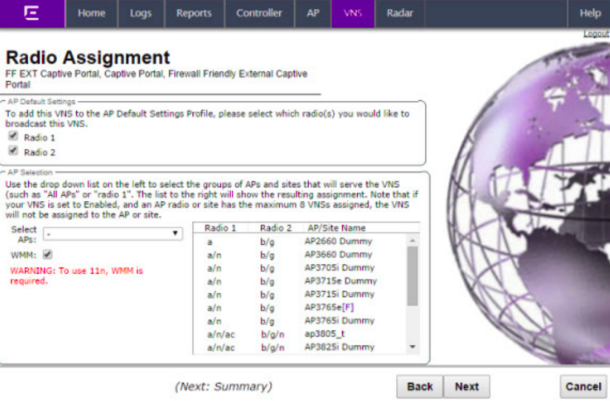
Radio Assignment
The Radio Assignment screen displays:
In “Select APs”, select the group of APs that will broadcast the Captive Portal VNS (e.g.: all radios).
Click next. The Summary screen displays.
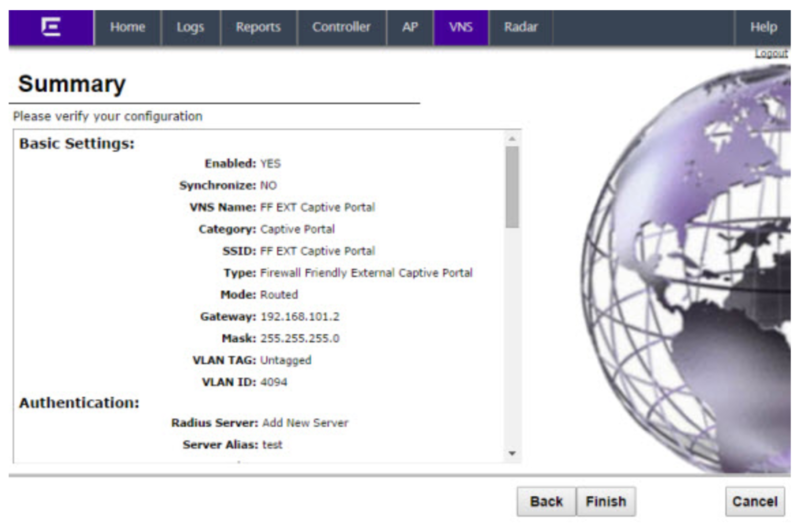
Summary
The Summary screen displays:
Confirm your data VNS configuration. To revise your configuration, click Back. To create your VNS, click Finish, and then click Close.
Roles
To use HTTP redirection an access control role must be defined on the controller with the following characteristics:
- The role allows the station to use DHCP, DNS and ARP.
- The role allows the station to communicate with the external captive portal server using HTTP or HTTPS.
- For FF-ECP, the role must allow the station to send traffic to the controller’s IP address on the VLAN containing the station’s traffic.
- The role blocks at least some HTTP traffic, although not HTTP traffic destined for the External Captive Portal or the port on the controller to which the ECP will redirect authenticated stations.
- The role must allow HTTP traffic for services used in the External Captive Portal (e.g. Facebook, Google Analytics, etc.).
If you have followed the VNS Wizard, the following policy rules must already be available:
- DNS (0.0.0.0/0:53, UDP)
- DHCP Server (0.0.0.0/0:67, UDP)
You’ll need to add policy rules to the services used by the CoffeeBean Captive Portal. See the list of hostnames in Walled garden and add the ones you use as matching patterns in the group Web Applications.
WLAN Services
If you have followed the VNS Wizard you’ll have a WLAN service already created.
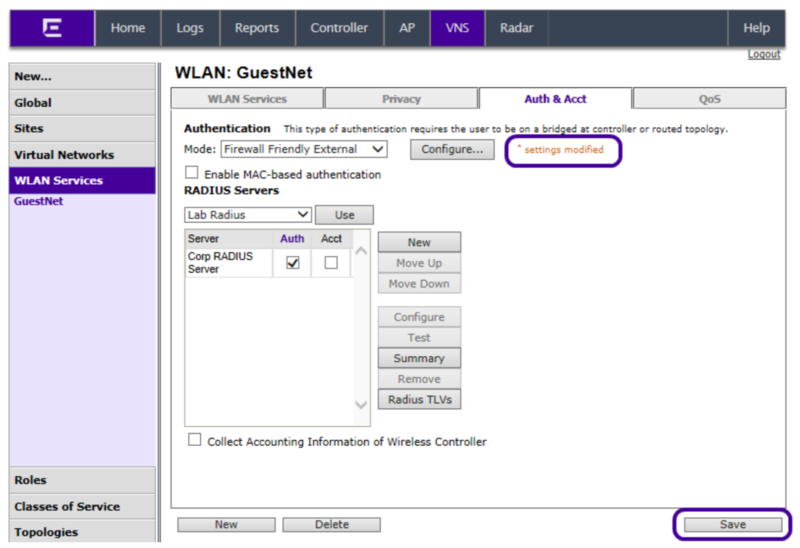
Once the WLAN Service exists, the FF-ECP configuration takes place on the Auth & Acct tab:
Captive Portal
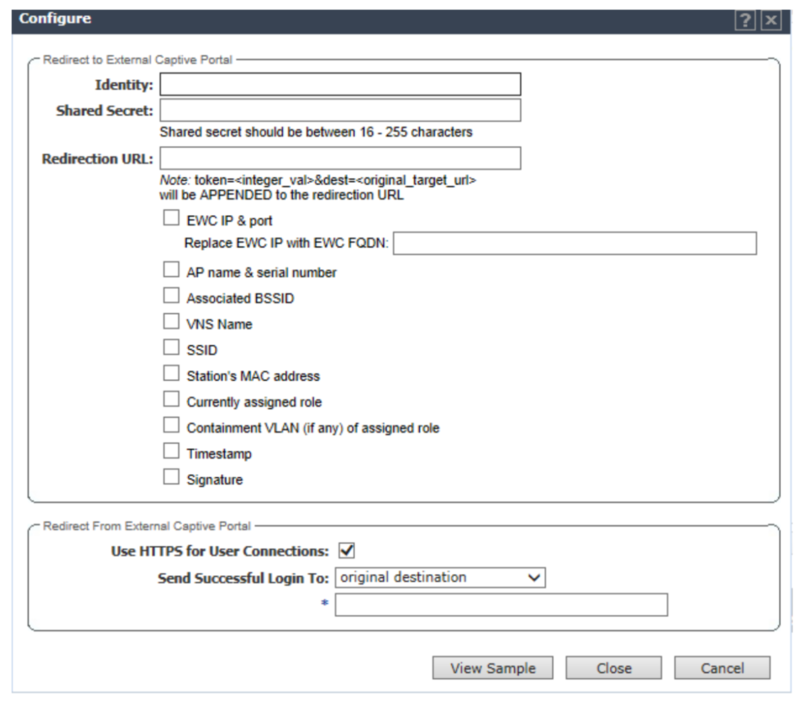
Configure the captive portal related addresses and the options that will be sent to the ECP. Start by clicking the Configure button.
Configure the following options:
- Identity: must be left empty
- Shared Secret: must be left empty
- Redirection URL: the provided captive portal login URL
- Check at least the following attributes:
- EWC IP & port
- Associated BSSID
- Station’s MAC address
- Use HTTPS for User connections: unchecked
- Send Successful Login To: select Captive Portal Session Page and configure the provided captive portal destination URL.
Once the appropriate options have been selected on the Configure dialog box, click Close. This returns you to the WLAN Service Auth & Acct tab. The changes made in the Configure dialog box have not been saved. This is indicated by the message “* settings modified” that appears next to the captive portal configuration button. You must click Save on the Auth & Acct tab for the changes to take effect.
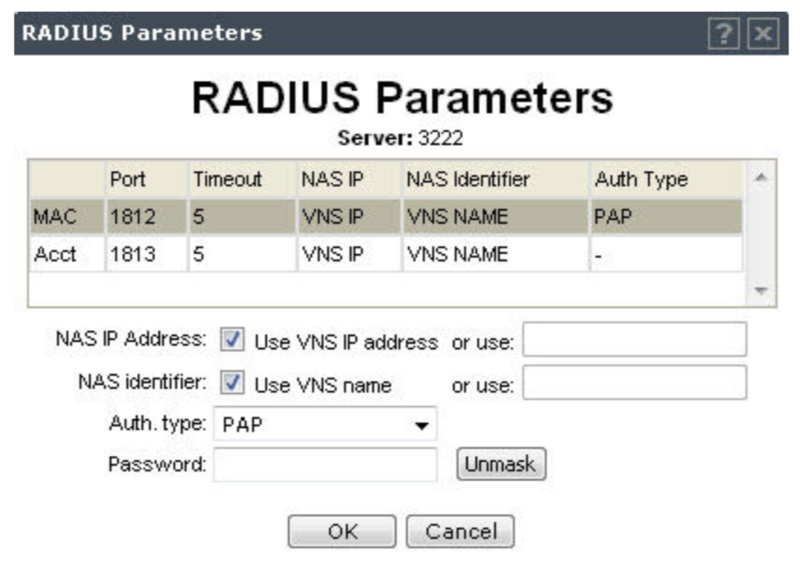
RADIUS Server
Click in the RADIUS server under Server and then click Configure. The RADIUS Parameters dialog is displayed:
Configure the following options:
- Auth. type: PAP
Customer Parameters
The summary of customer specific parameters is:
Basic Settings
- Redirection URL: the provided captive portal login URL
- Authentication
- Hostname/IP: the RADIUS server hostname according to your environment/region.
- Shared Secret: the provided RADIUS client secret.
- Policy Rules: see the list of hostnames in Walled garden.
- Captive Portal
- Send Successful Login To: configure the provided captive portal destination URL.