FortiGate 30E
(→IPv4 Policy) |
|||
| (16 intermediate revisions by one user not shown) | |||
| Line 3: | Line 3: | ||
== User & Device == | == User & Device == | ||
=== RADIUS Server === | === RADIUS Server === | ||
| − | Go to User & Device > RADIUS Servers and configure the following options: | + | Go to '''User & Device > RADIUS Servers''' and configure the following options: |
| − | * Name: CoffeeBean-radius-server | + | * '''Name:''' CoffeeBean-radius-server |
| − | * Authentication Method: Specify | + | * '''Authentication Method:''' Specify |
| − | * Method: PAP | + | * '''Method:''' PAP |
| − | * IP/Name: The RADIUS IP will depend on your environment/region. You can check the IP for your region at our Captive Portal Configuration Page | + | * '''IP/Name:''' The RADIUS IP will depend on your environment/region. You can check the IP for your region at our Captive Portal Configuration Page |
| − | * Primary Shared Secret: Use the Shared Secret provided by CoffeeBean | + | * '''Primary Shared Secret:''' Use the Shared Secret provided by CoffeeBean |
| + | |||
| + | [[File:RADIUS Server.png|752px]] | ||
=== User Groups === | === User Groups === | ||
| − | Go to User & Device > User Groups to create a group. Perform the following settings: | + | Go to '''User & Device > User Groups''' to create a group. Perform the following settings: |
| + | |||
| + | * '''Name:''' CoffeeBean-user-group | ||
| + | * '''Type:''' Firewall | ||
| + | * '''Remote groups:''' Create a new one and configure the following options: | ||
| + | ** '''Remote Server:''' CoffeeBean-radius-server | ||
| + | ** '''Group Name:''' insert any group name | ||
| − | + | [[File:2fortinet-user-groups.png|752px]] | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
== SSID == | == SSID == | ||
| − | Go to WiFi Controller > SSID click on Create New > SSID and setup the following settings: | + | Go to '''WiFi Controller > SSID''' click on '''Create New > SSID''' and setup the following settings: |
| − | * Interface Name: CoffeeBean-guest-ssid | + | * '''Interface Name:''' CoffeeBean-guest-ssid |
| − | * Type: WiFi SSID | + | * '''Type:''' WiFi SSID |
| − | * Traffic Mode: Tunnel to Wireless Controller | + | * '''Traffic Mode:''' Tunnel to Wireless Controller |
| − | * Address: (e.g.: 192.168.30.1/255.255.255.0) | + | * '''Address:''' (e.g.: 192.168.30.1/255.255.255.0) |
| − | * Restrict Access: RADIUS Accounting | + | * '''Restrict Access:''' RADIUS Accounting |
| − | * DHCP Server: Ativo | + | * '''DHCP Server:''' Ativo |
| − | * SSID: (e.g.: CoffeeBean) | + | * '''SSID:''' (e.g.: CoffeeBean) |
| − | * Security Mode: Captive Portal Portal | + | * '''Security Mode:''' Captive Portal Portal |
| − | * Type: Authentication | + | * '''Type:''' Authentication |
| − | * Authentication Portal: External: Enter your captive portal URL (e.g.: https://wifi-staging.socialidnow.com/portals/<portal name>/auth) | + | * '''Authentication Portal:''' External: Enter your captive portal URL (e.g.: https://wifi-staging.socialidnow.com/portals/<portal name>/auth) |
| − | * User Groups: CoffeeBean-user-group | + | * '''User Groups:''' CoffeeBean-user-group |
| − | * Broadcast SSID: Enabled | + | * '''Broadcast SSID:''' Enabled |
| − | * Block Intra-SSID Traffic: Enabled | + | * '''Block Intra-SSID Traffic:''' Enabled |
| − | * Redirect after Captive Portal:Enter your captive portal URL (e.g.: https://wifi-staging.socialidnow.com/portals/<portal name>) | + | * '''Redirect after Captive Portal:''' Enter your captive portal URL (e.g.: https://wifi-staging.socialidnow.com/portals/<portal name>) |
| + | |||
| + | [[File:3fortinet-ssid-1.png|752px]] | ||
| + | |||
| + | [[File:4fortinet-ssid-2.png|752px]] | ||
== Policy & Objects == | == Policy & Objects == | ||
=== Addresses (Walled Garden) === | === Addresses (Walled Garden) === | ||
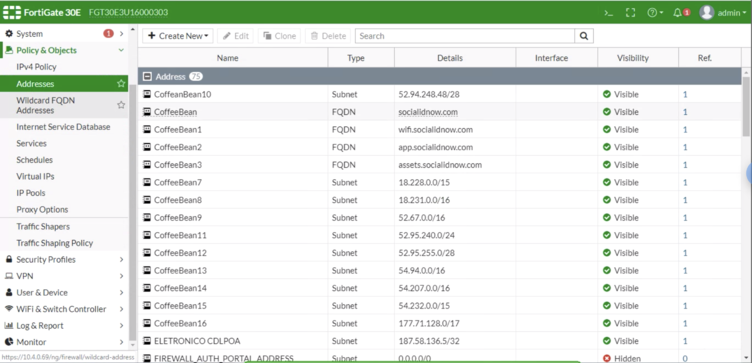
| − | Go to Policy & Objects > Addresses to setup the Walled Garden. For this settings it is recommended to use DNS. If the controller does not accept the recommended way (DNS), the user can configure using IPs. For each input the following options: | + | Go to '''Policy & Objects > Addresses''' to setup the Walled Garden. For this settings it is recommended to use DNS. If the controller does not accept the recommended way (DNS), the user can configure using IPs. For each input the following options: |
| − | * Name: Input any name to control what does each IP or DNS means (e.g.: Facebook 1, Facebook 2) | + | * '''Name:''' Input any name to control what does each IP or DNS means (e.g.: Facebook 1, Facebook 2) |
| − | * Type: FQDN (recommended) or IP/Netmask | + | * '''Type:''' FQDN (recommended) or IP/Netmask |
| − | * Subnet / IP range or FQDN: IPs or DNS listed in this page documentation, if FQDN option available. Important: for FQDN entries, it’s necessary to input the complete hostnames (subdomain + domain). | + | * '''Subnet / IP range or FQDN:''' IPs or DNS listed in this page [[Walled Garden for the Social Login|documentation]], if FQDN option available. Important: for FQDN entries, it’s necessary to input the complete hostnames (subdomain + domain). |
| − | * Show in Address List: checked | + | * '''Show in Address List:''' checked |
| − | * Static Route Configuration: unchecked | + | * '''Static Route Configuration:''' unchecked |
| + | |||
| + | [[File:5fortinet-walled-garden.png|752px]] | ||
=== Address Group === | === Address Group === | ||
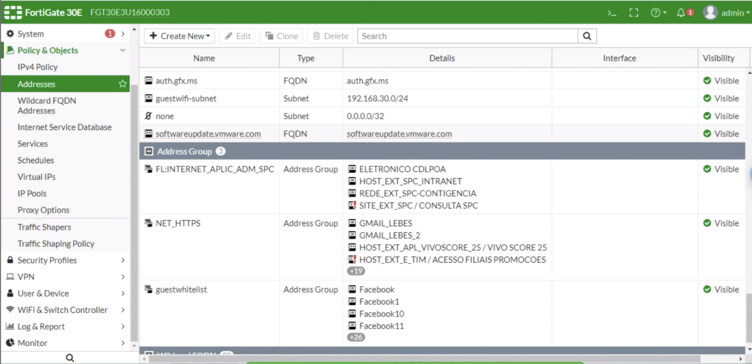
| − | Go to Addresses and click on Create New > Address Group and configure the following options: | + | Go to '''Addresses''' and click on '''Create New > Address Group''' and configure the following options: |
| − | * Category: IPv4 Group | + | * '''Category:''' IPv4 Group |
| − | * Group Name: CoffeeBean-walled-garden | + | * '''Group Name:''' CoffeeBean-walled-garden |
| − | * Members: [click on “+” button and select all domains previously added] | + | * '''Members:''' [click on “+” button and select all domains previously added] |
| − | + | [[File:6fortinet-address-group.png|752px]] | |
| − | + | ||
| − | + | === IPv4 Policy === | |
| + | ==== DNS Policy ==== | ||
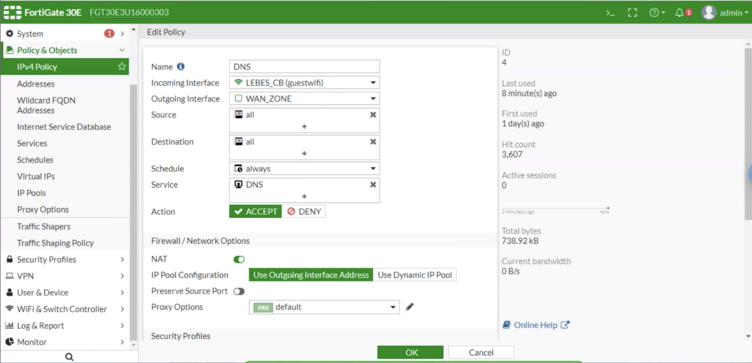
| − | * Name: DNS | + | Go to '''IPv4 Policy''' and click on '''Create New''' and configure the following options: |
| − | * Incoming Interface: CoffeeBean-guest-ssid | + | |
| − | * Outgoing Interface: <your WAN connection> | + | * '''Name:''' DNS |
| − | * Source: all | + | * '''Incoming Interface:''' CoffeeBean-guest-ssid |
| − | * Destination Address: all | + | * '''Outgoing Interface:''' <your WAN connection> |
| − | * Schedule: always | + | * '''Source:''' all |
| − | * Service: DNS | + | * '''Destination Address:''' all |
| − | * Action: ACCEPT | + | * '''Schedule:''' always |
| − | * NAT: enabled | + | * '''Service:''' DNS |
| − | * Enable this policy: Active | + | * '''Action:''' ACCEPT |
| + | * '''NAT:''' enabled | ||
| + | * '''Enable this policy:''' Active | ||
| + | |||
| + | [[File:7fortinet-policy.png|752px]] | ||
Get the policy ID on the policies list and run the CLI command bellow: | Get the policy ID on the policies list and run the CLI command bellow: | ||
| − | config firewall policy | + | config firewall policy |
| − | edit <policy_id> | + | edit <policy_id> |
| − | set captive-portal-exempt enable | + | set captive-portal-exempt enable |
| − | end | + | end |
| − | === Policy for Unauthenticated Users === | + | ==== Policy for Unauthenticated Users ==== |
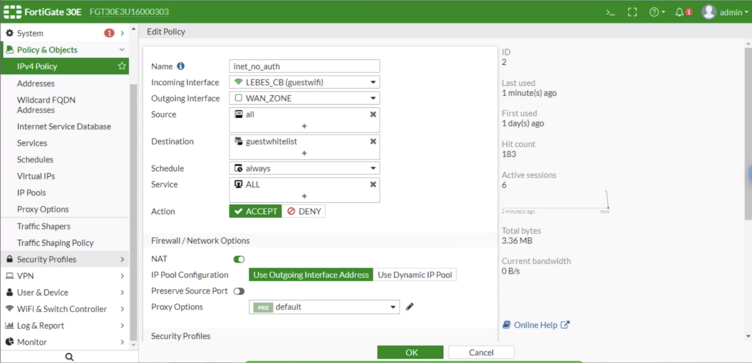
| − | Go to IPv4 Policy and click on Create New and configure the following options: | + | Go to '''IPv4 Policy''' and click on '''Create New''' and configure the following options: |
| − | * Name: CoffeeBean-unauth-policy | + | * '''Name:''' CoffeeBean-unauth-policy |
| − | * Incoming Interface: CoffeeBean-guest-ssid | + | * '''Incoming Interface:''' CoffeeBean-guest-ssid |
| − | * Outgoing Interface: <your WAN connection> | + | * '''Outgoing Interface:''' <your WAN connection> |
| − | * Source: all | + | * '''Source:''' all |
| − | * Destination Address: CoffeeBean-walled-garden | + | * '''Destination Address:''' CoffeeBean-walled-garden |
| − | * Schedule: always | + | * '''Schedule:''' always |
| − | * Service: ALL | + | * '''Service:''' ALL |
| − | * Action: ACCEPT | + | * '''Action:''' ACCEPT |
| − | * NAT: enabled | + | * '''NAT:''' enabled |
| − | * Enable this policy: Active | + | * '''Enable this policy:''' Active |
| + | |||
| + | [[File:8fortinet-unauthenticated.png|752px]] | ||
Get the policy ID on the policies list and run the CLI command bellow: | Get the policy ID on the policies list and run the CLI command bellow: | ||
| Line 101: | Line 117: | ||
end | end | ||
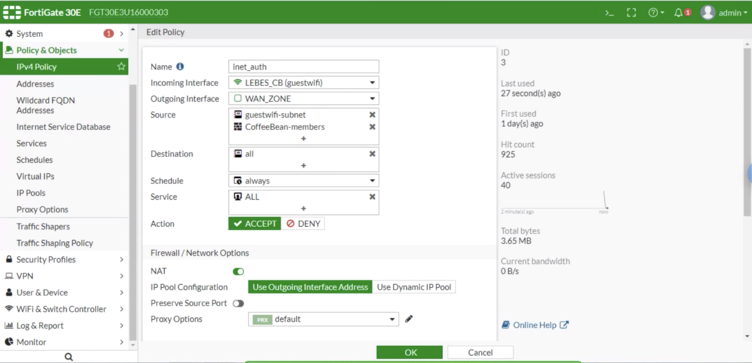
| − | === Policy for Authenticated Users === | + | ==== Policy for Authenticated Users ==== |
| + | |||
| + | Go to '''Policy & Objects > Addresses''', configure a new input for the subnet configured on the SSID: | ||
| + | |||
| + | * '''Name:''' CoffeeBean-ssid-address | ||
| + | * '''Type:''' IP/Netmask | ||
| + | * '''Subnet / IP Range:''' (e.g.: 192.168.30.0/255.255.255.0) | ||
| + | * '''Interface:''' any | ||
| + | |||
| + | Go to '''IPv4 Policy''' click on '''Create New''' and configure the following options: | ||
| − | + | * '''Name:''' CoffeeBean-auth-policy | |
| + | * '''Incoming Interface:''' CoffeeBean-guest-ssid | ||
| + | * '''Outgoing Interface:''' <your WAN connection> | ||
| + | * '''Source:''' select CoffeeBean-user-group and CoffeeBean-ssid-address | ||
| + | * '''Destination Address:''' all | ||
| + | * '''Schedule:''' always | ||
| + | * '''Service:''' ALL | ||
| + | * '''Action:''' ACCEPT | ||
| + | * '''NAT:''' enabled | ||
| + | * '''Enable this policy:''' Active | ||
| − | + | [[File:9fortinet-authenticated.png|752px]] | |
| − | + | ||
| − | + | ||
| − | + | ||
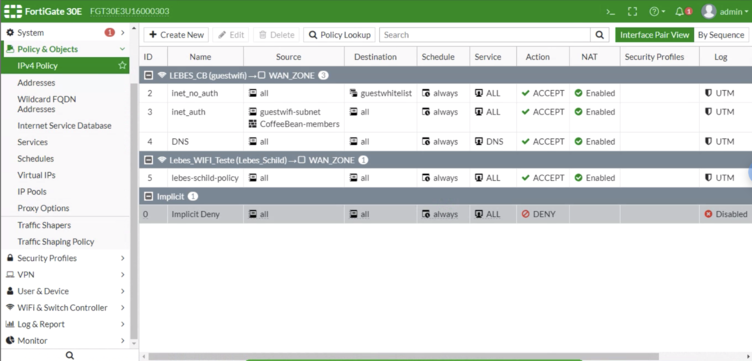
| − | + | ==== Policies Summary ==== | |
| − | + | [[File:10fortinet-policies-summary.png|752px]] | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
Latest revision as of 20:00, 27 December 2021
This guide describes the configuration steps to enable an external captive portal in the Forti AP.
Contents |
User & Device
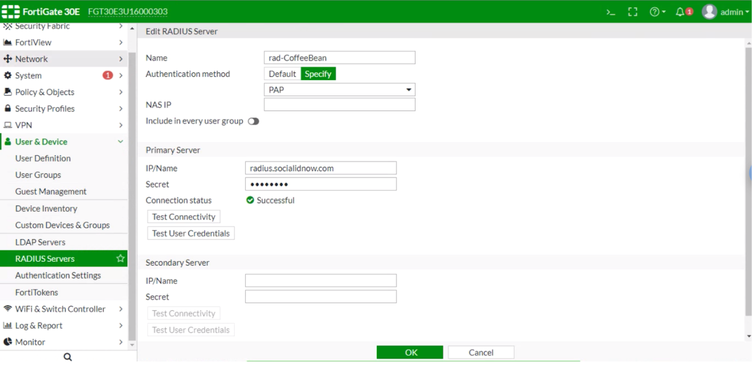
RADIUS Server
Go to User & Device > RADIUS Servers and configure the following options:
- Name: CoffeeBean-radius-server
- Authentication Method: Specify
- Method: PAP
- IP/Name: The RADIUS IP will depend on your environment/region. You can check the IP for your region at our Captive Portal Configuration Page
- Primary Shared Secret: Use the Shared Secret provided by CoffeeBean
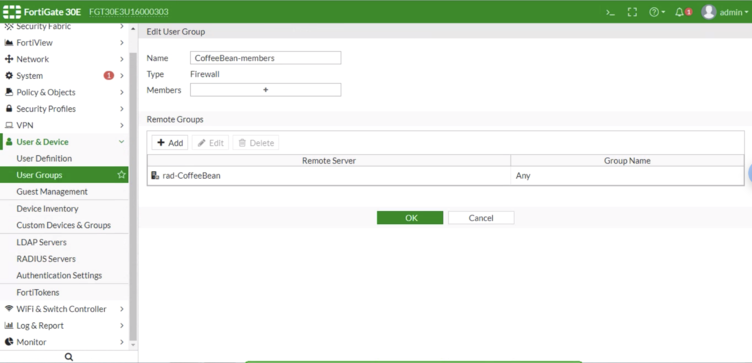
User Groups
Go to User & Device > User Groups to create a group. Perform the following settings:
- Name: CoffeeBean-user-group
- Type: Firewall
- Remote groups: Create a new one and configure the following options:
- Remote Server: CoffeeBean-radius-server
- Group Name: insert any group name
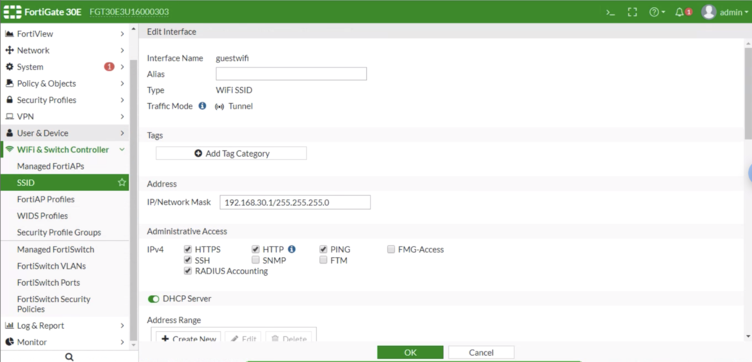
SSID
Go to WiFi Controller > SSID click on Create New > SSID and setup the following settings:
- Interface Name: CoffeeBean-guest-ssid
- Type: WiFi SSID
- Traffic Mode: Tunnel to Wireless Controller
- Address: (e.g.: 192.168.30.1/255.255.255.0)
- Restrict Access: RADIUS Accounting
- DHCP Server: Ativo
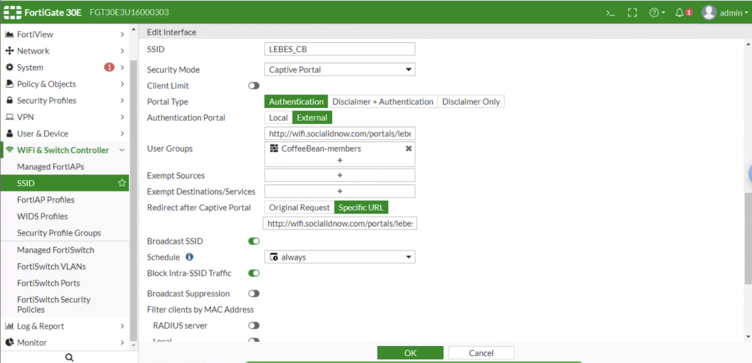
- SSID: (e.g.: CoffeeBean)
- Security Mode: Captive Portal Portal
- Type: Authentication
- Authentication Portal: External: Enter your captive portal URL (e.g.: https://wifi-staging.socialidnow.com/portals/<portal name>/auth)
- User Groups: CoffeeBean-user-group
- Broadcast SSID: Enabled
- Block Intra-SSID Traffic: Enabled
- Redirect after Captive Portal: Enter your captive portal URL (e.g.: https://wifi-staging.socialidnow.com/portals/<portal name>)
Policy & Objects
Addresses (Walled Garden)
Go to Policy & Objects > Addresses to setup the Walled Garden. For this settings it is recommended to use DNS. If the controller does not accept the recommended way (DNS), the user can configure using IPs. For each input the following options:
- Name: Input any name to control what does each IP or DNS means (e.g.: Facebook 1, Facebook 2)
- Type: FQDN (recommended) or IP/Netmask
- Subnet / IP range or FQDN: IPs or DNS listed in this page documentation, if FQDN option available. Important: for FQDN entries, it’s necessary to input the complete hostnames (subdomain + domain).
- Show in Address List: checked
- Static Route Configuration: unchecked
Address Group
Go to Addresses and click on Create New > Address Group and configure the following options:
- Category: IPv4 Group
- Group Name: CoffeeBean-walled-garden
- Members: [click on “+” button and select all domains previously added]
IPv4 Policy
DNS Policy
Go to IPv4 Policy and click on Create New and configure the following options:
- Name: DNS
- Incoming Interface: CoffeeBean-guest-ssid
- Outgoing Interface: <your WAN connection>
- Source: all
- Destination Address: all
- Schedule: always
- Service: DNS
- Action: ACCEPT
- NAT: enabled
- Enable this policy: Active
Get the policy ID on the policies list and run the CLI command bellow:
config firewall policy edit <policy_id> set captive-portal-exempt enable end
Policy for Unauthenticated Users
Go to IPv4 Policy and click on Create New and configure the following options:
- Name: CoffeeBean-unauth-policy
- Incoming Interface: CoffeeBean-guest-ssid
- Outgoing Interface: <your WAN connection>
- Source: all
- Destination Address: CoffeeBean-walled-garden
- Schedule: always
- Service: ALL
- Action: ACCEPT
- NAT: enabled
- Enable this policy: Active
Get the policy ID on the policies list and run the CLI command bellow:
config firewall policy edit <policy_id> set captive-portal-exempt enable end
Policy for Authenticated Users
Go to Policy & Objects > Addresses, configure a new input for the subnet configured on the SSID:
- Name: CoffeeBean-ssid-address
- Type: IP/Netmask
- Subnet / IP Range: (e.g.: 192.168.30.0/255.255.255.0)
- Interface: any
Go to IPv4 Policy click on Create New and configure the following options:
- Name: CoffeeBean-auth-policy
- Incoming Interface: CoffeeBean-guest-ssid
- Outgoing Interface: <your WAN connection>
- Source: select CoffeeBean-user-group and CoffeeBean-ssid-address
- Destination Address: all
- Schedule: always
- Service: ALL
- Action: ACCEPT
- NAT: enabled
- Enable this policy: Active